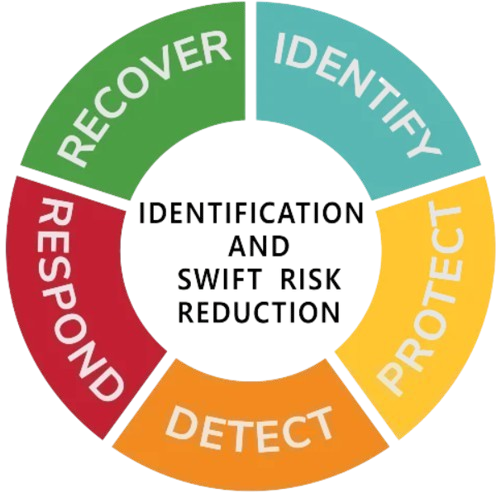
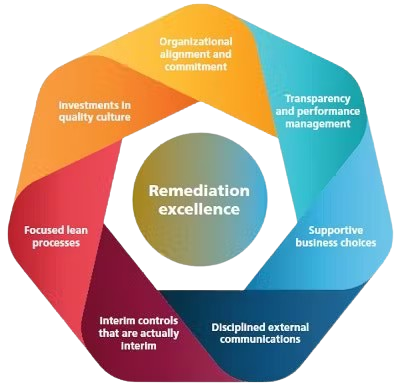
Our work is further designed to deliver a customized solution:
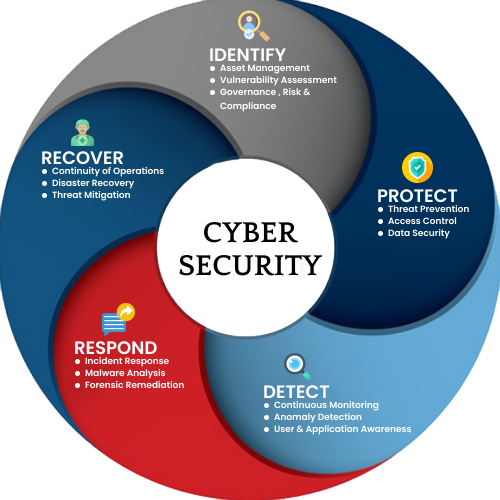
In today’s corporate landscape where everything is electronic & digital there is a great need and call to promote cybersecurity culture at an individual level, national, international and also at an organizational level to help minimize risks from a human perspective in cyberspace.
RNR have been the cyber security and process improvement consultant for several organizations ranging from Government sectors to various private businesses. Through our journey in this position, we have found that assembly of philosophies continue to surface that we have come to use, which help us through the challenges and decisions.
Here are a few of philosophies and mantras that we hold:
These mantras also help us learn new ways to look at the problems and find solutions!
- Protect and Secure information. In this IT based society everything runs on its information/data and it is a must to secure it. The data can be electronic, documents and also portable media. There is already a widespread awareness of its criticality and the need to find solution.
- Individual User Each employee is captiously important to the security of the data and information. And an individual’s uncalled for actions can result in a big loss for the company. which means that each employee who deals with the data and critical information should be part of the defense mechanism. All individuals should be trained to keep an open eye towards identifying a threat such as issues that seems unusual or strange series of mails or sudden changes in their workstations etc. cyber security involves each employee to be trained, educated and re-educated on how to defend computer/USB drives/information and the security of the company.
- Keep an eye of a spy on all New Programs, Projects, Tools, etc. The security professionals need to be more sensitive in this area as the new project ideas in the marketplace are more vulnerable to the threats. Organized cyber-criminals use social network sites for targeting and distributing computer malware/worms. The point being made is that the company needs to look at any new application, tool etc with a same mind-set of a hacker.
- If it’s made very Convenient then the Security measures are usually lacking, thus risking the profiles of the Organizations. For example, the usage of Laptop at any place which are otherwise protected on the hardwired LAN.
- Inclusion of Security as a blue-print of your new projects, especially for the startups. Instead of fixing a security problem under-way your project, it is advised to include Cyber-Security at the design stage. This will serve in the long-term interest of the Organization. Lost or breached data would be an expensive affair
Align your security strategy with your business
Building a custom security plan that is both industry-specific and aligned to your security maturity demands a partner with the expertise and resources to help you remotely or onsite. The IBM Security Strategy and Risk services team is that trusted resource.

Protect your digital assets, users and data
To help you build a foundation of trust in your interactions, you should enable the right user to have the right access to the right data. IBM Security Digital Trust solutions can help.

Manage your defenses against growing threats.
When every second counts, you need a unified defense to identify, orchestrate and automate your response to threats. IBM Security Threat Management solutions help you thrive in the face of cyber uncertainty. Security information and event management (SIEM)

Modernize your security with an open, multicloud strategy
We help you scale up with efficiency by working as your long-term extension of your team or even as a short-term strategic partner, as per your need. 11. (Turnkey - TNM)
Align your security strategy with your business
Building a custom security plan that is both industry-specific and aligned to your security maturity demands a partner with the expertise and resources to help you remotely or onsite. The IBM Security Strategy and Risk services team is that trusted resource.

Protect your digital assets, users and data
To help you build a foundation of trust in your interactions, you should enable the right user to have the right access to the right data. IBM Security Digital Trust solutions can help.
Manage your defenses against growing threats.
When every second counts, you need a unified defense to identify, orchestrate and automate your response to threats. IBM Security Threat Management solutions help you thrive in the face of cyber uncertainty. Security information and event management (SIEM)

Modernize your security with an open, multicloud strategy
We help you scale up with efficiency by working as your long-term extension of your team or even as a short-term strategic partner, as per your need. 11. (Turnkey – TNM)
How we work
We work as your reliable and trusted partner. As an Analyst. Consultant. Technologist, Information Security Consultant. Designer and as a Data Scientist. RNR is an expert & diverse team that helps your business escalate to the next level.
Our work is further designed to deliver a customized solution:

Consultative Design -
Our designs evolve around business decisions you need to make and implement. We map the most fitting course to get your business to the desired heights.

Customer Engagement –
We help you scale up with efficiency by working as your long-term extension of your team or even as a short-term strategic partner. We can also work on full-time engagement; as per your need.

Holistic Approach –
Our expert team gathers data from all ends and fill your team with knowledge gaps. Further, integrating available information, filtering the insights that helps you in decision making and process management.

Single point deliverables –
We understand your questions and the need for an answer paired with a plan of action, in catering to all these needs we deliver to the point presentations that are easy to understand yet rich in visuals and infographics. Our outputs are interactive and best solution providers.