Web application VAPT
It refers to the process of conducting a vulnerability assessment and penetration testing of an organization’s web applications. This type of testing includes scanning web applications to identify vulnerabilities that could be exploited by attackers. It is typically performed by a third-party security firm and is an important component of a comprehensive cybersecurity program. The goal of web application VAPT is to identify and remediate vulnerabilities before an attacker can exploit them and compromise the security of an organization’s web applications.
Our Approach to Web Application Security Testing
Our web application security testing service is designed to detect both technical and business logic vulnerabilities in your websites. With detailed instructions and concrete recommendations, we provide you with a comprehensive analysis of any potential weaknesses.

There are 2 types of Web applications VAPT:
- External web application VAPT: It refers to the process of conducting a vulnerability assessment and penetration testing of an organization’s externally facing web applications
- Internal web application VAPT: It refers to the process of conducting a vulnerability assessment and penetration testing of an organization’s internally facing web applications.
Web servers and the application code running on those as a simple website or web portal, are vulnerable to various attacks. In one type of attack, the hacker can simply deface the pages, while in other serious types, the attacker can potentially steal data and disrupt website operations.
What we do:
Our VAPT services include the following steps:
- Vulnerability assessment: The penetration tester gathers information about the web application, such as its source code, architecture, and configuration.
- Scanning: The penetration tester scans the web application for vulnerabilities, such as SQL injection, cross-site scripting, and weak passwords.
- Exploitation: The penetration tester attempts to exploit the vulnerabilities that were identified in the scanning phase.
- Reporting: The penetration tester reports the results of the penetration test to the organization, including the vulnerabilities that were identified and the recommendations for remediation.
VAPT services can be a valuable tool for organizations of all sizes. It can help organizations identify and fix vulnerabilities in their web applications that could be exploited by attackers. This can help to prevent data breaches and other security incidents.

Internal network penetration testing
An internal network pen test is performed to help gauge what an attacker could achieve with initial access to a network. An internal network pen test can mirror insider threats, such as employees intentionally or unintentionally performing malicious actions.
What we do:
Our Internal network penetration testing services include the following steps:
- Information gathering: The penetration tester gathers information about the organization’s internal network, such as its IP addresses, hostnames, and open ports. This information is used to identify vulnerabilities that may not be detected by automated scanning tools.
- Vulnerability scanning: The penetration tester scans the organization’s internal network for vulnerabilities, such as open ports, weak passwords, and misconfigured security settings.
- Penetration testing: The penetration tester attempts to exploit the vulnerabilities that were identified in the scanning and assessment phases. This is done to verify that the vulnerabilities are exploitable and to identify the impact of an attack.
- Reporting: The penetration tester reports the results of the assessment to the organization, including the vulnerabilities that were identified, the risks associated with the vulnerabilities, and the recommendations for remediation.
Services for internal network penetration testing can be a useful resource for businesses of all sizes. It can assist businesses in locating and repairing network flaws that an attacker might exploit. RNR aids in preventing safety issues and data breaches.

External network penetration testing
An external network pen test is designed to test the effectiveness of perimeter security controls to prevent and detect attacks as well as identify weaknesses in internet-facing assets such as web, mail, and FTP servers.
What we do:
RNR’s External network penetration testing services includes the following steps:
- Information gathering: The penetration tester gathers information about the organization’s external network, such as its IP addresses, hostnames, and open ports. This information is used to identify vulnerabilities that may not be detected by automated scanning tools.
- Vulnerability scanning: The penetration tester scans the organization’s external network for vulnerabilities, such as open ports, weak passwords, and misconfigured security settings.
- Penetration testing: The penetration tester attempts to exploit the vulnerabilities that were identified in the scanning and assessment phases. This is done to verify that the vulnerabilities are exploitable and to identify the impact of an attack.
- Reporting: The penetration tester reports the results of the assessment to the organization, including the vulnerabilities that were identified, the risks associated with the vulnerabilities, and the recommendations for remediation.
External network penetration testing services can be a valuable tool for organizations of all sizes. It can help organizations identify and fix vulnerabilities in their networks that could be exploited by attackers. RNR helps to prevent data breaches and other security incidents.

- Integrated proprietary, open-source and commercial tools
- Intelligent automated testing engine selects the ideal combination of tools based on internal benchmarks
- Our reports provide step-by-step POCs and detailed fix information with code and config examples
- Identifies both technical (OWASP Top 10, WASC 25, etc) and business logic vulnerabilities
- We create an in-depth map of your web-application business-logic and workflow
- Experts manually create specific test-cases for your web-application logic and workflow
- Access to our real-time security dashboard to track your projects, issues and fixes.
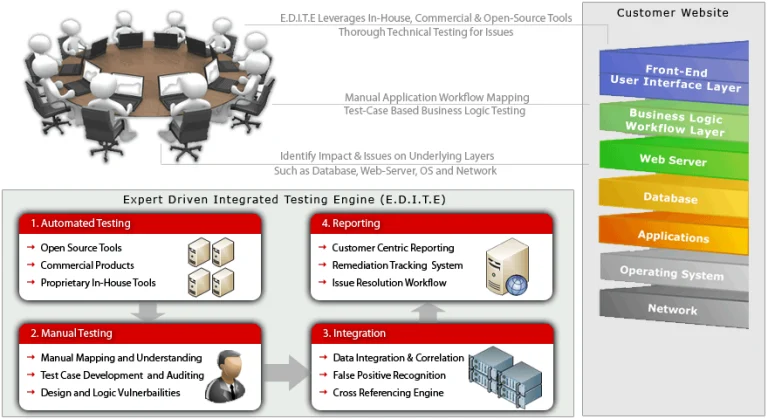
Our Approach
Web Application Security Testing
Unlike traditional website security services that only focus on using automated scanners, we take a comprehensive approach by thoroughly examining your business logic and web-application data flow. By doing so, we are able to identify vulnerabilities that are specifically related to your workflows. By combining both automated and expert-driven manual testing, we ensure that the end result for your web-applications is the best possible.
Leave us message

