Cloud Penetration Methodology
RnR uses widely acknowledged and tested industrial standards and frameworks to conduct cloud penetration testing. The underlying framework’s bottom layer is based on principles such as CIS Benchmarking and goes well beyond the initial framework.
The examination of vulnerabilities, which includes examining the output from various security tools and testing procedures, is part of cloud security assessment. Cloud Account Testing Methodology, Cloud Server Testing Methodology, and Cloud-Based Web App Testing Methodology are only a few of the duties that make up a cloud security assessment.
We Comply with all the Top IT Security Testing Guidelines
Cloud Account Testing Methodology
The classifications of vulnerabilities that RnR discursive technique for cloud penetration testing overlays are not limited. The procedure for performing Cloud Account Security Testing is as follows:

Tools Used
We make use of tools from the following (not a complete list):
Prowler
Scout suite
Cloud Sploit
Cloud Mapper
Sky Ark
Lunar
Reporting
The goal of the reporting stage is to deliver, rank, and prioritize all cloud security concerns, as well as present project stakeholders with a concise and actionable report that includes proof. At RnR, we create a complete report based on significant research to give our client with a proper set of options and resolving steps. Our cloud security services are facilitated in the best interests of our clients, which are presented in every way.
Cloud Server Testing Methodology
Auditing
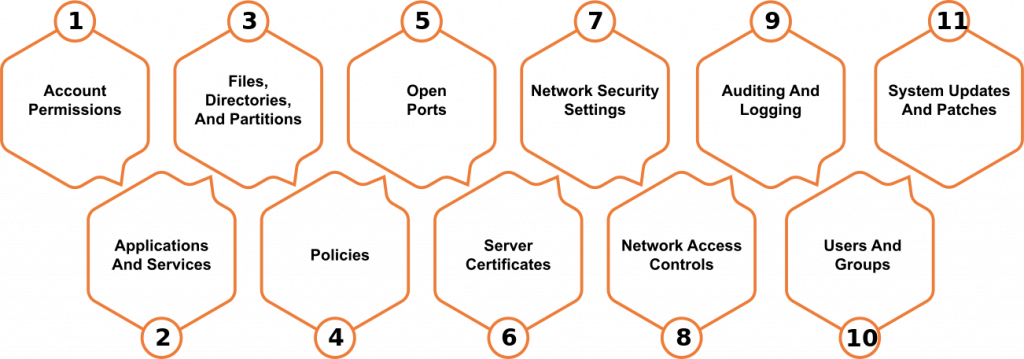
Tools Used
Nexpose
Nessus
Lynis
Nmap
Reporting
The reporting step is intended to deliver, rank, and prioritize findings and provide project stakeholders with a clear and actionable report, complete with evidence. At RnR, we consider this phase to be the most important and we take great care to ensure we’ve communicated the value of our cloud pen testing service and findings thoroughly.
Cloud Web Based App Testing Methodology
Reconnaissance
This is the first stage of cloud-based web app testing, when a set of procedures is used to obtain all the necessary information about the target cloud environment. The diversity of networks is investigated, as well as the detection of active hosts. Reconnaissance can be accomplished in a variety of ways, the most common of which being port scanning and the use of programs such as NetcatPreserve and ping. Getting file permission, injecting into OS platforms, acquiring user account information, and creating trust connections are some of the methodological techniques for conducting reconnaissance.
Example testing includes Conduct Search Engine Discovery and Reconnaissance for Information Leakage, Search Engine Recon, App Enumeration and App Fingerprinting, Identify app entry point.
Vulnerability Analysis Analysis
- Configuration Management
- Session Management
- Data Input Validation
- Client-Side Testing
- Authentication Testing
- Authorization Testing
- Testing for Error Handling


Exploitation
The penetration tester examines the data gathered to launch an attack on the cloud server. Exploration for vulnerabilities is done meticulously, ensuring a higher chance of successful exploitation. This has a direct bearing on the project’s success. The pen tester employs complex techniques to gain access to sensitive data, which he then uses to carry out nefarious operations by exploiting the vulnerabilities discovered. The attack on the most privileged users, known as root, is the next phase in this process.
The pentester instigates multiple and regular interference with the compromised devices. This allows them to build backdoors within the application to gain a secondary access for executing further exploitation in future.
Example testing includes Conduct Search Engine Discovery and Reconnaissance for Information Leakage, Search Engine Recon, App Enumeration and App Fingerprinting, Identify app entry point.
Tools
- Burp suit
- BeEF
- Grabber
- Vega
- Zad Attack Proxy
- Acunetix
- SQLmap
Reporting
The goal of the reporting stage is to deliver, rank, and prioritize findings while also providing project stakeholders with a clear and actionable report that includes proof. This is the most crucial phase for us at RnR, and we take great care to make sure we’ve clearly articulated the importance of our cloud pen testing service and findings.
Trusted by International Brand






























What is Cloud Penetration Testing?
Cloud penetration testing is used to evaluate a cloud system's strengths and weaknesses to strengthen its overall security posture. Risks, vulnerabilities, and gaps can all be identified through cloud penetration testing. Vulnerabilities that can be exploited. Determine how to make the most of any exploitation-related access.
Cloud security is a critical feature of any online computing environment. Cloud Penetration Tests aims to recognize risks and vulnerabilities on the following platforms:
1. Cloud Based Servers:
2. Web Applications:
3. Networks:
4. Online Systems:
5. Hosts:
6. Network Devices (Routers, switches etc.)
Leave us massage










